HLD009 - Vulnerability Management (Amazon Inspector)
Introduction
Purpose
This document describes an approach to vulnerability management suitable for the AWS Cloud environment.
The vulnerability management system should:
be fully integrated with used AWS services - EC2, ECR and Lambda
send real time alerts about detected vulnerabilities
provide a reporting mechanism, with details about recommended remediation steps whenever possible
automatically remediate the security issues whenever possible
be well documented.
Changelog
Revision | Date | Description |
|---|---|---|
| 23.07.2024 | Initial document |
Background
Vulnerability management is the process of continuously assessing, reporting on and managing security vulnerabilities across systems.
Amazon Inspector provides an automated service for vulnerability detection and assessment for the Amazon Elastic Compute Cloud, Elastic Container Registry and AWS Lambda.
NVD/CVSS scores are used as the basis of severity assessment for detected vulnerabilities.
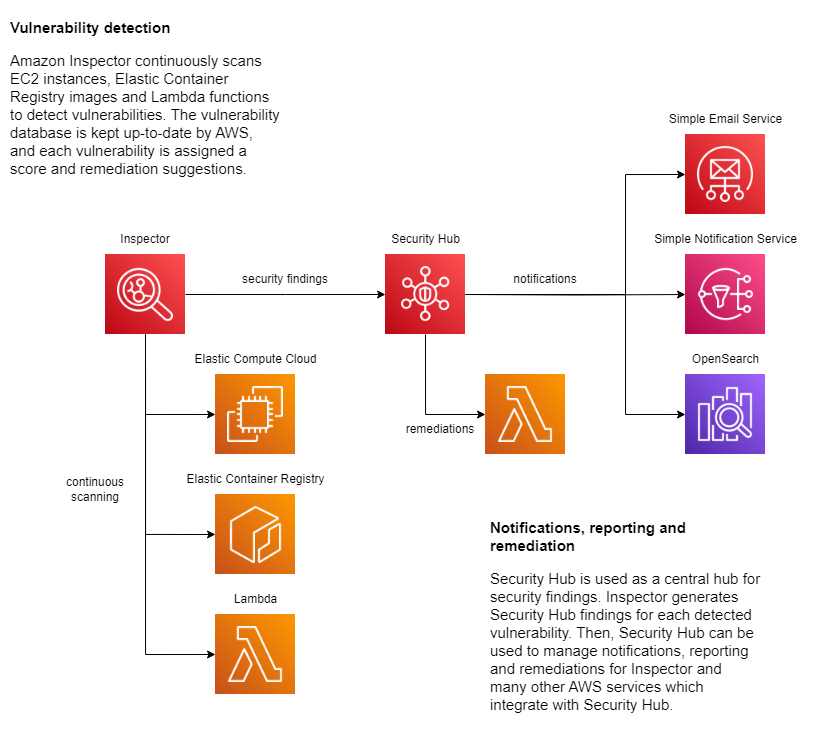
Amazon Inspector integrates seamlessly with other AWS Services, providing continuous scanning of EC2 instances through the AWS Systems Manager Agent, ECR container images on push and on vulnerability database updates, and AWS Lambda dependencies and code. Findings are propagated to Security Hub which can then be used for reporting and notifications.
Architecture diagram
Amazon Inspector pricing
Amazon Inspector has no upfront costs, the cost depends only on the number of EC2 instances, container images and Lambda functions scanned each month.
Assuming the Europe (Ireland) region, the pricing table presents as follows:
Average number of Amazon EC2 instances scanned per month* | $1.2528 per instance |
Number of container images scanned initially on-push to Amazon ECR per month | $0.09 per image |
Number of automated rescans for container images in Amazon ECR configured for continuous scanning per month | $0.01 per rescan |
Average number of AWS Lambda functions scanned per month** | $0.30 per Lambda function |
Average number of AWS Lambda functions scanned per month with both Lambda Standard and Code Scanning** | $0.30 + $0.60 per Lambda function |
Average number of EC2 instances - an instance running for a full month is counted as one, if an instance has been active less than a full month it is counted proportionally.
Example:
1 instance running for a full month
1 instance running for half of the month
equate on average to 1.5 EC2 instances per month - approximately $1.9 monthly.
Average number of AWS Lambda functions scanned per month - similar to the EC2 instance average, if a Lambda function doesn’t exist for the entire month, the cost is scaled proportionally.
Please note that Lambda Code Scanning is a new feature, but as per current version of Terraform AWS provider it is bugged.
Multi-account aggregation
In a multi-account environment, it is possible to aggregate Amazon Inspector results into a delegated administrator account. However, this account needs to be designated by the Organization management account, and there can be only one for the entire organization.
In situations where that’s not acceptable, limited aggregation can be done on Security Hub’s side. Vulnerabilities detected by Inspector are reported to Security Hub on each account, and then aggregated into a single, chosen Security Hub account. In the case of Security Hub, this account does not have to be delegated by the Organization management account.
While Security Hub is a good central point for storing data in an unified format, it is not as good at presenting the data as the dedicated Inspector dashboard.
Updated: Since our discussion with DTIT didn't produce a positive outcome regarding providing us with a delegated administrator for Security Hub purposes, we will need to setup remedations & notifications per account.
Scanning occurrence & frequency
Amazon Inspector performs Network reachability scans for EC2 instances once every 24 hours.
Upon activation, Amazon Inspector scans all SSM-managed instances in your account. Amazon Inspector initiates new vulnerability scans of SSM-managed EC2 instances in the following situations:
When you launch a new EC2 instance.
When you install new software on an existing EC2 instance (Linux only).
When Amazon Inspector adds a new common vulnerabilities and exposures (CVE) item to its database, and that CVE is relevant to your EC2 instance (Linux only).
When you first activate ECR scanning, Inspector scans eligible images pushed in the last 30 days.
By default, images are scanned for a Lifetime duration.
You can configure a different duration through the console or API - to 30 or 180 days from the image push → reference: Configuring the ECR automated re-scan duration
Amazon Inspector initiates new vulnerability scans of container images in the following situations:
Whenever a new container image is pushed.
Whenever Amazon Inspector adds a new common vulnerabilities and exposures (CVE) item to its database, and that CVE is relevant to that container image (continuous scanning only).
Upon activation, Amazon Inspector scans all Lambda functions invoked or updated in the last 90 days in your account.
Inspector initiates vulnerability scans of Lambda functions in the following situations:
As soon Inspector discovers an existing Lambda function.
When a new Lambda function to the Lambda service is deployed.
When an update to the application code or dependencies of an existing Lambda function or its layers is deployed.
Whenever Amazon Inspector adds a new common vulnerabilities and exposures (CVE) item to its database, and that CVE is relevant to your function.
Amazon Inspector monitors each Lambda function throughout its lifetime until it's either deleted or excluded from scanning.
Notifications, reporting and custom remediations
Because Inspector integrates well with Security Hub, it is possible to re-use/develop Security Hub based solutions for notifications/reporting/remediations, limiting the duplication of work.
OpenSearch Integration
A custom Security Hub remediation or individual solution can be developed to submit Inspector findings to OpenSearch/ElasticSearch, but this is still an open topic, which will be addressed during Security Hub deployment.
Limitations
Amazon EC2, ECR & Lambda + Lambda Code Scanning in Inspector is limited to certain OS and code versions. For details please refer to: https://docs.aws.amazon.com/inspector/latest/user/supported.html
Implementation details
Inspector should be enabled on all accounts using a Terraform module, and configured to scan EC2, ECR and Lambda.
Security Hub integration should start working automatically once both services are enabled.
Security Hub email remediations should be configured to send notifications about vulnerabilities to the responsible parties (e.g. resource owner, security team).
Security Hub remediation should be developed to submit inspector findings to OpenSearch/ElasticSearch.
A solution to generate aggregate reports should be developed for Security Hub and configured to send out reports for Inspector-related findings.
Expected Outcomes
EC2 instances, ECR images, and Lambdas are continuously scanned for known vulnerabilities.
Detected vulnerabilities are automatically assigned a severity score and, if possible, suggested remediation steps.
People responsible for the vulnerable systems are notified in real time about detected issues.
Aggregate reports of detected vulnerabilities and their remediation status are generated.
Information about detected vulnerabilities is submitted to OpenSearch/ElasticSearch for further processing.