LLD003-002 - GuardDuty
Introduction
Purpose
The primary objective of this document is to provide a comprehensive overview of the functionality and capabilities of AWS GuardDuty in terms of detecting threats and monitoring unauthorized activities within all prod and pre-prod accounts.
Changelog
Revision | Date | Description |
|---|---|---|
| 11.07.2024 | Initial document |
Related documents
LLD003-001 - Continuous Compliance - rules, controls, remediations
Background
AWS GuardDuty is a service designed to secure your AWS accounts and applications by constantly monitoring for threats. With its full features enabled, it offers a comprehensive shield against potential security hazards.
Here's why we need to use it:
Proactive Threat Identification: GuardDuty operates non-stop, scanning billions of data points across your AWS usage, including AWS CloudTrail, Amazon VPC Flow Logs, and DNS logs. This helps in detecting any suspicious behaviour or threats in real time, allowing for quick response.
Smart Threat Detection: GuardDuty not only detects threats but also uses machine learning and integrated threat intelligence feeds to understand and predict abnormal behaviours or patterns, reducing the risk of unexpected attacks.
Detect Unusual Activities: Using its anomaly detection feature, GuardDuty can spot unusual activities, like a sudden surge in data transfers or new activity in a region you've never used before, which might indicate a security concern.
Monitoring Multiple AWS Accounts: GuardDuty can monitor threats across multiple AWS accounts, making it an ideal solution for large organizations with several accounts. This ensures no part of your business is left vulnerable.
Automatic Updates & Scalability: GuardDuty is a managed service and gets updated regularly, ensuring your organization benefits from the most recent threat detection algorithms. Furthermore, it scales with your AWS usage, protecting all your resources no matter how your business grows.
Maintaining Compliance: GuardDuty helps in meeting compliance requirements by offering continuous monitoring of any malicious or unauthorized behaviour across your AWS infrastructure, thereby assisting you in adhering to standards like PCI DSS, HIPAA, GDPR, etc.
Seamless Integration: Findings from GuardDuty can be easily integrated with other AWS services like CloudWatch Events and AWS Security Hub. This allows further analysis and even triggers automated remediation processes when required.
When it comes to supported services in full mode, GuardDuty analyzes and monitors the logs from AWS CloudTrail, Amazon VPC Flow Logs, and DNS logs, also separately we can activate Kubernetes audit logs, RDS login activity, S3 logs, EBS volumes, Runtime monitoring, and Lambda network activity logs. Using these data sources and features (if enabled), GuardDuty generates security findings for your account.
Architecture diagram
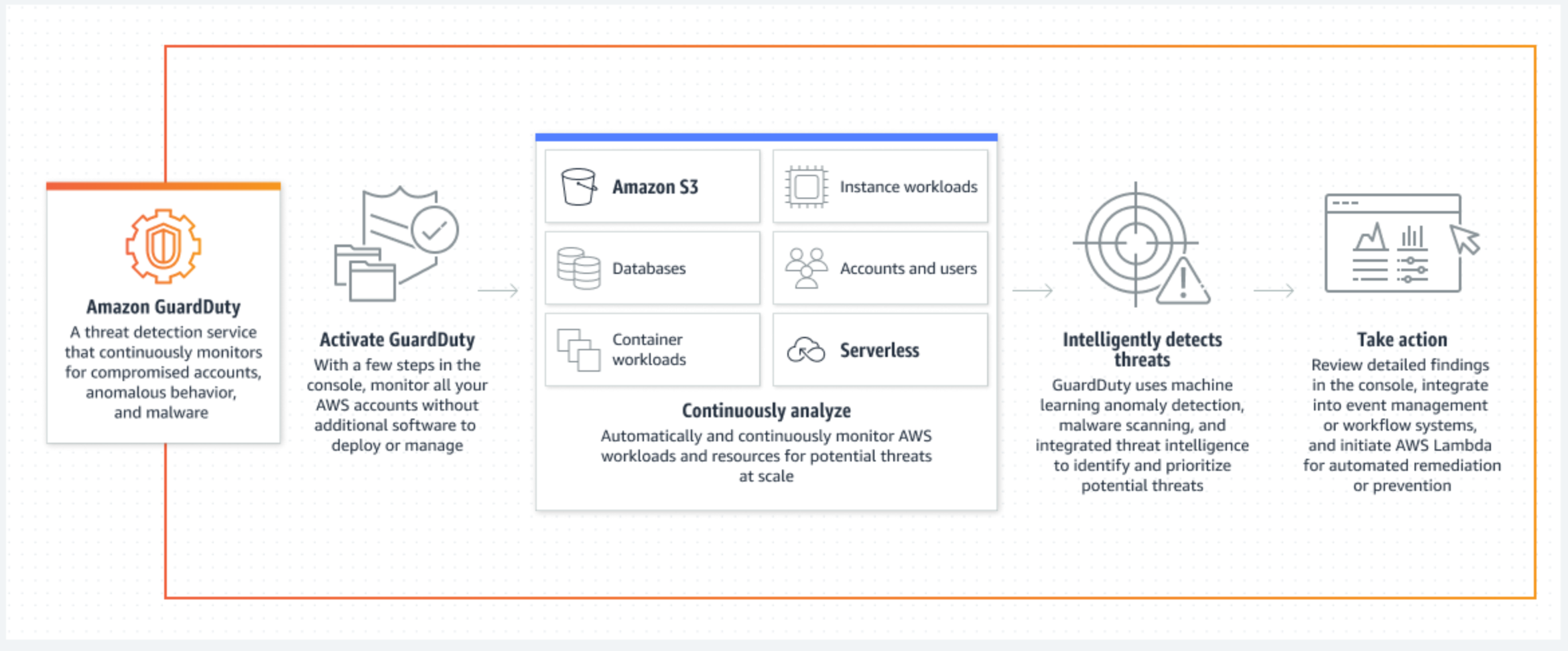
Explanation
As soon as Amazon GuardDuty will be active, or we will turn on a specific type of protection within GuardDuty, it begins working with the associated Foundational data sources in your AWS environment. These data sources encompass events coming from VPC flow logs, DNS logs, and AWS CloudTrail event and management logs. GuardDuty scrutinizes these events to detect possible security issues and produces findings in your account.
Foundational data sources
Finding types
Reconnaissance: Indicators of potential reconnaissance by an attacker include atypical API behaviour, scanning of ports within the same virtual private cloud (VPC), abnormal patterns of unsuccessful login attempts, or probing of unsecured ports originating from a recognized malicious IP address.
Instance compromise: Activity indicating an instance compromise, such as the presence of cryptocurrency mining, the utilization of malware employing domain generation algorithms (DGAs), outbound denial of service (DoS) actions, an abnormally large volume of network traffic, unusual network protocols, outbound communication from the instance to a recognized malicious IP, temporary Amazon EC2 credentials accessed by an external IP address, and the exfiltration of data through the use of DNS.
Account compromise: Typical indicators of an account compromise involve various patterns, such as API requests originating from uncommon geolocation or through an anonymizing proxy, efforts to disable CloudTrail logging, abnormal launches of instances or infrastructure, deployments of infrastructure in atypical regions, the unauthorized extraction of credentials, suspicious login activity in databases, and API calls originating from recognized malicious IP addresses.
Bucket compromise: Indications of a compromised bucket involve various activities, such as suspicious data access patterns suggesting the misuse of credentials, uncommon Amazon S3 API activity originating from a remote host, unauthorized access to Amazon S3 from recognized malicious IP addresses, and API calls made by a user without a previous history of accessing the bucket or originating from an unusual location. GuardDuty is a monitoring service that continuously analyzes CloudTrail S3 data events, including GetObject, ListObjects, and DeleteObject, to detect potentially suspicious activity across all of your Amazon S3 buckets.
Malware detection: When GuardDuty detects suspicious behaviour that indicates the presence of malicious software in Amazon EC2 instances or container workloads, it initiates a malware detection scan. This process involves creating temporary replicas of the Amazon Elastic Block Store (EBS) volumes attached to the affected instances or workloads. The volume replicas are then scanned for various types of malware, including trojans, worms, crypto miners, rootkits, bots, and more. The purpose of this scan is to identify any malicious elements that could compromise the workloads, exploit resources for nefarious purposes, or gain unauthorized access to data. GuardDuty's Malware Protection feature generates detailed findings that provide contextual information, helping to validate the source of the suspicious behaviour. These findings can be directed to the appropriate administrators for further investigation and can also trigger automated remediation processes to mitigate the identified risks.
Container compromise: Activity identifying possible malicious or suspicious behaviour in container workloads is detected by continuously monitoring and profiling Amazon EKS clusters by analyzing its Amazon EKS audit logs and container runtime activity. Those findings we can add to 3 categories, Policy (exposed dashboard, admin access to default service account, anonymous access granted), Malicious access( data discovery, exfiltration or modification from tor, malicious IPs, successful anonymous access), Suspicious behaviour ( execution in system pod, a container with sensitive mount, privilege container).
RDS protection: analyzes and profiles RDS login activity for potential access threats to your Amazon Aurora databases (Amazon Aurora MySQL-Compatible Edition and Aurora PostgreSQL-Compatible Edition).
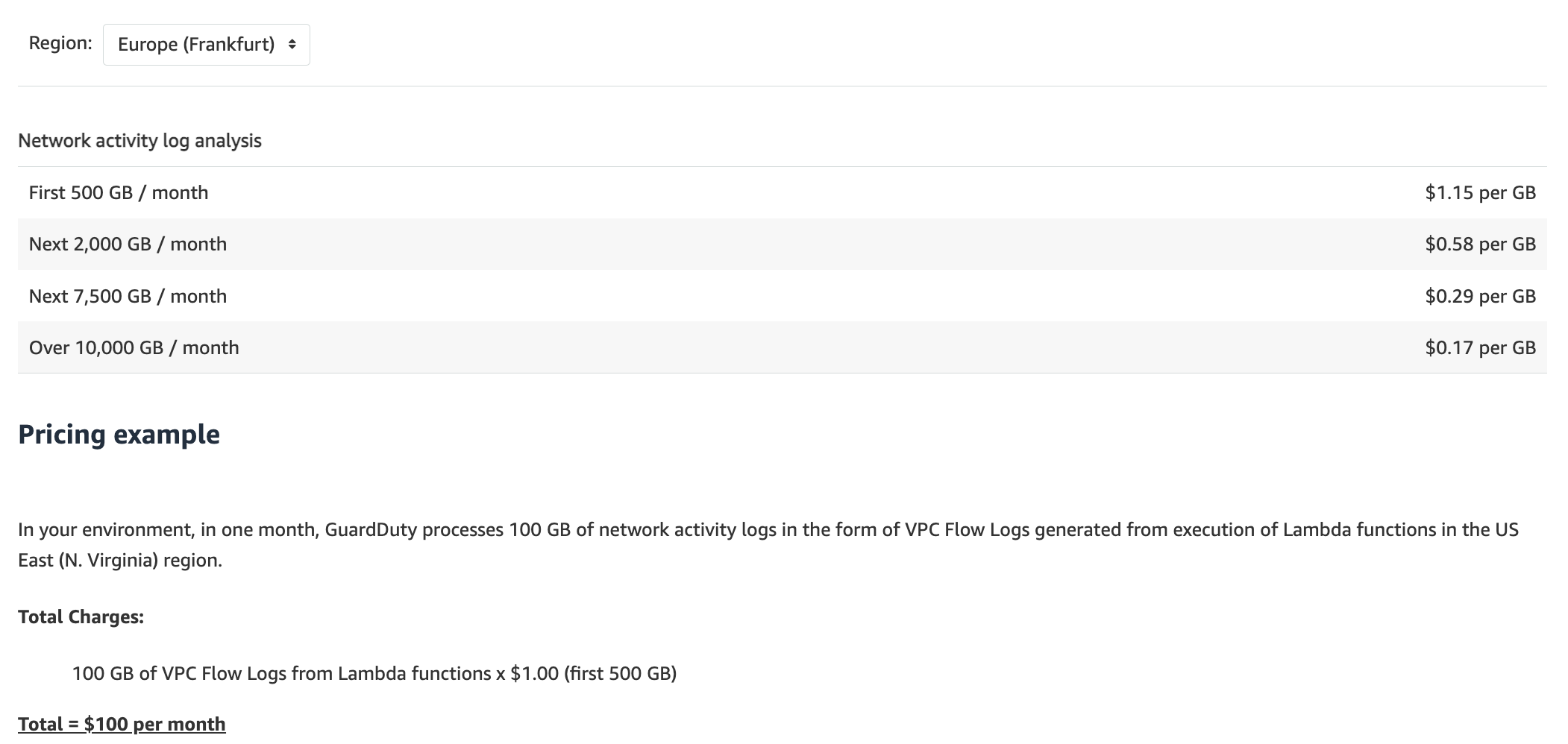
Lambda protection: continuously monitors network activity, starting with VPC Flow Logs, from your serverless workloads to detect threats such as Lambda functions maliciously repurposed for unauthorized cryptocurrency mining, or compromised Lambda functions that are communicating with known threat actor servers.
Route 53 Resolver DNS Firewall: you have the option to activate a new Managed Domain List on Amazon Route 53 Resolver DNS Firewall. This list allows you to block domains that are considered to have a low reputation or are known/suspected to be malicious, based on the threat intelligence provided by Amazon GuardDuty. This integration enables customers using GuardDuty to block domains using the same threat intelligence that is utilized to monitor and alert potential DNS threats for their AWS accounts.
Please see the detailed list of supported finding in AWS documentation Finding types - Amazon GuardDuty.
Implementation details
GuardDuty is extremely easy to implement, it only requires us to enable the service and straight away it starts to monitor our environment. However, implementation requires couple more services to be fully operational:
Configure exporting GuardDuty findings to an Amazon S3 bucket
Set up GuardDuty finding alerts through SNS (GuardDuty integrates with Amazon EventBridge, which can be used to send findings data to other applications and services for processing. With EventBridge you can use GuardDuty findings to initiate automatic responses to your findings by connecting finding events to targets such as AWS Lambda functions, Amazon EC2 Systems Manager automation, and Amazon Simple Notification Service (SNS))
We need to remember that GuardDuty is a Regional service. Any user with administrator privileges in an AWS account can enable GuardDuty, however, following the security best practice of least privilege, it is recommended that you create an IAM role, user, or group to manage GuardDuty specifically.
By utilizing AWS Organizations, GuardDuty offers the capability to designate a specific account within the organization as the delegated administrator for GuardDuty. This designation can only be performed by the management account of the organization. When an account is designated as a delegated administrator, it becomes an administrator account for GuardDuty. This account automatically enables GuardDuty in the designated Region and gains the necessary permissions to enable and manage GuardDuty for all accounts within the organization in that specific Region. The remaining accounts within the organization can then be viewed and added as GuardDuty member accounts, associated with the delegated administrator account.
Pricing
GuardDuty prices are based on the volume of service logs, events, workloads, or data analyzed. GuardDuty pricing tiers include foundational pricing, which is the default level of service coverage, as well as optional protection plans pricing. When you activate GuardDuty for the first time, you will automatically have foundational protections and optional protection plans turned on, with the exception of Amazon EKS Runtime Monitoring, which can be activated separately. While you can turn off any optional protection features at any time, the foundational protections are required for active GuardDuty accounts. Analyzed service logs are filtered for cost optimization and directly integrated with GuardDuty, which means you don’t have to activate or pay for them separately.
Foundational threat detection pricing
To detect unauthorized and unexpected activity in your AWS environment, GuardDuty analyzes and processes data from foundational data sources to detect anomalies involving AWS Identity and Access Management (IAM) access keys and Amazon Elastic Compute Cloud (Amazon EC2).
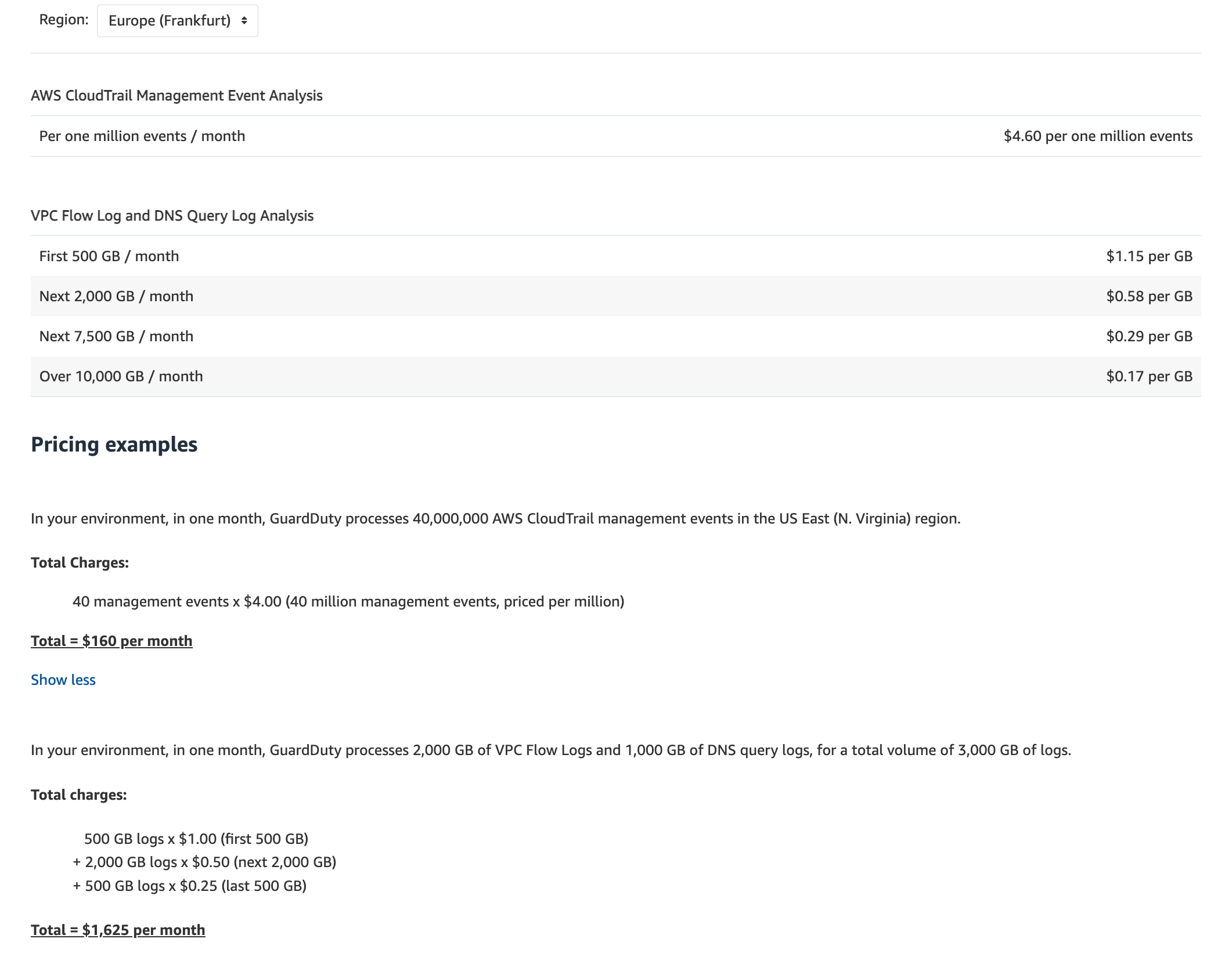
AWS CloudTrail management event analysis: GuardDuty continuously analyzes CloudTrail management events. Management events (also known as control plane) provide information about management operations that are performed on resources in your AWS account. CloudTrail management event analysis is charged per 1 million events per month and is prorated.
Amazon Virtual Private Cloud (VPC) Flow Log and DNS query log analysis: GuardDuty continuously analyzes Amazon VPC Flow Logs and Domain Name System (DNS) query logs. VPC Flow Log and DNS query log analysis is charged per gigabyte (GB) per month. Both VPC Flow Log and DNS query log analyses are discounted with volume.
GuardDuty comes with a 30-day trial on the AWS Free Tier. During the free trial period and thereafter, you can always monitor your estimated monthly spend on the GuardDuty console usage page, broken down by data source.
Optional protection plans
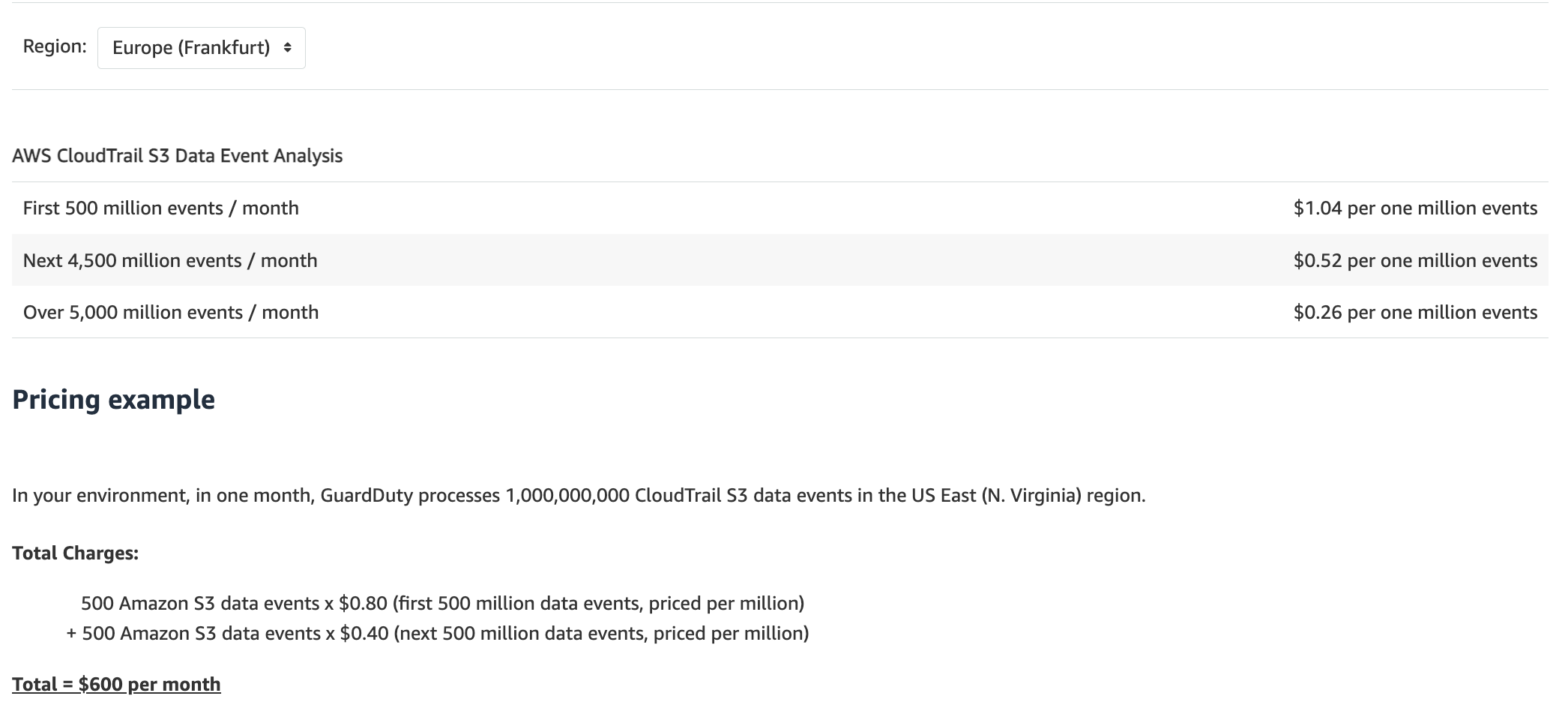
S3 Protection - GuardDuty monitors threats against your Amazon S3 resources by analyzing AWS CloudTrail management events and CloudTrail S3 data events. When the GuardDuty S3 Protection feature is turned on, GuardDuty continuously analyzes authenticated CloudTrail S3 data events, monitoring access and activity in your S3 buckets. CloudTrail S3 data event analysis is charged per 1 million events per month, is prorated, and is discounted with volume.
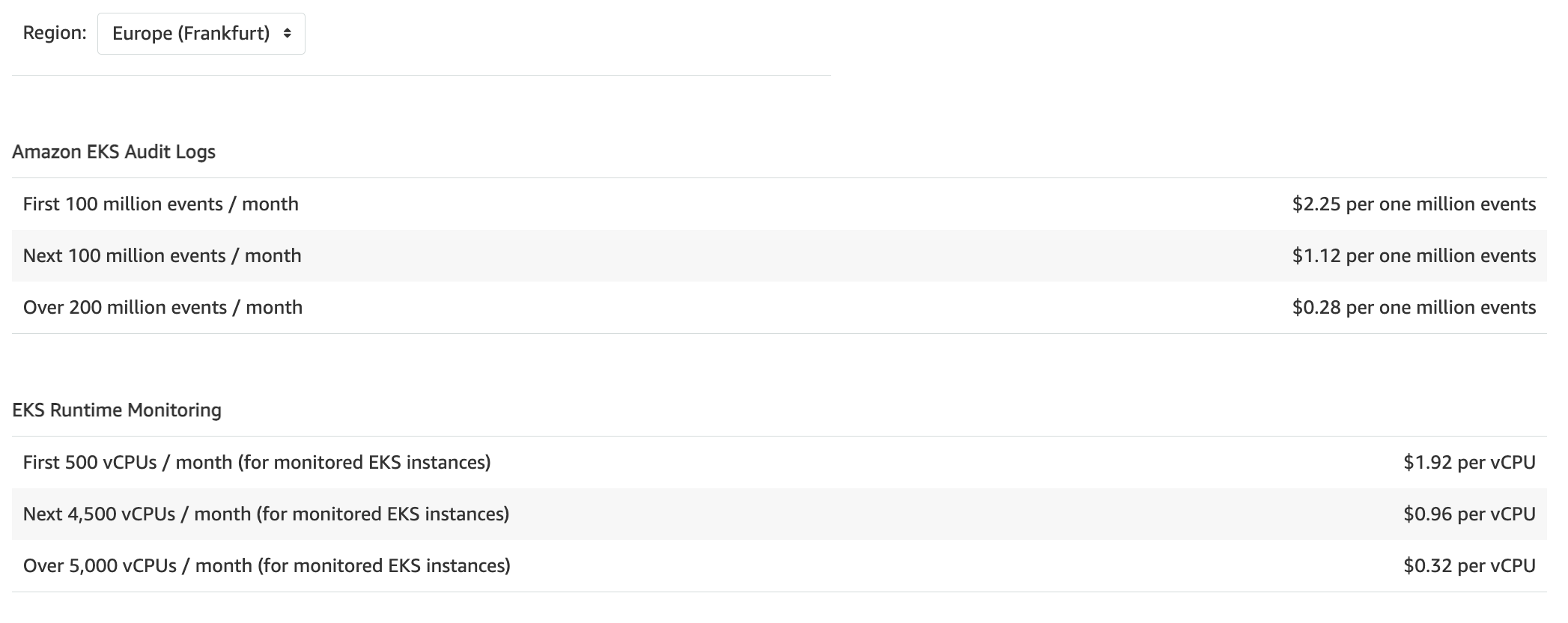
EKS Protection - When the GuardDuty EKS Protection feature is activated, GuardDuty continuously analyzes Amazon EKS audit logs and optimizes costs by processing only events that are used for security analysis. Amazon EKS audit log analysis is charged per 1 million audit logs per month, is prorated, and is discounted with volume.
When the GuardDuty EKS Protection feature is activated, and EKS runtime monitoring is turned on and there are active GuardDuty agents deployed on workloads in the account, GuardDuty will immediately begin monitoring your Amazon EKS instance runtime activities, such as file access, process execution, and network connections. EKS Runtime Monitoring pricing is based on the number and size of protected EKS workloads, measured in virtual CPUs (vCPUs).
If EKS Runtime Monitoring is enabled for your account, you will not be charged for analysis of VPC Flow Logs from instances where the GuardDuty agent is deployed and active.
If you configure EKS Runtime Monitoring to automatically deploy the GuardDuty security agent, this could result in additional resource utilization, and will also create VPC endpoints in VPCs used to run Amazon EKS clusters. Learn more about Amazon EKS add-ons.
Customers will not be charged for associated networking bandwidth costs for event delivery.

Malware protection - When the GuardDuty Malware Protection feature is turned on, Amazon Elastic Compute Cloud (EC2) instance or container workloads with detected behavior indicative of malware will have a replica of their attached Amazon Elastic Block Store (Amazon EBS) volumes scanned for possible malware. The charge for GuardDuty Malware Protection is based on the total and prorated GB volume of Amazon EBS data scanned each month. Configurable guardrails that you set up can help you control spend, such as setting up notifications when usage exceeds a specified limit and the ability to control which Amazon EC2 instances to scan using tags. Also, attached EBS volumes over 1 TB (1,024 GB) are not scanned.
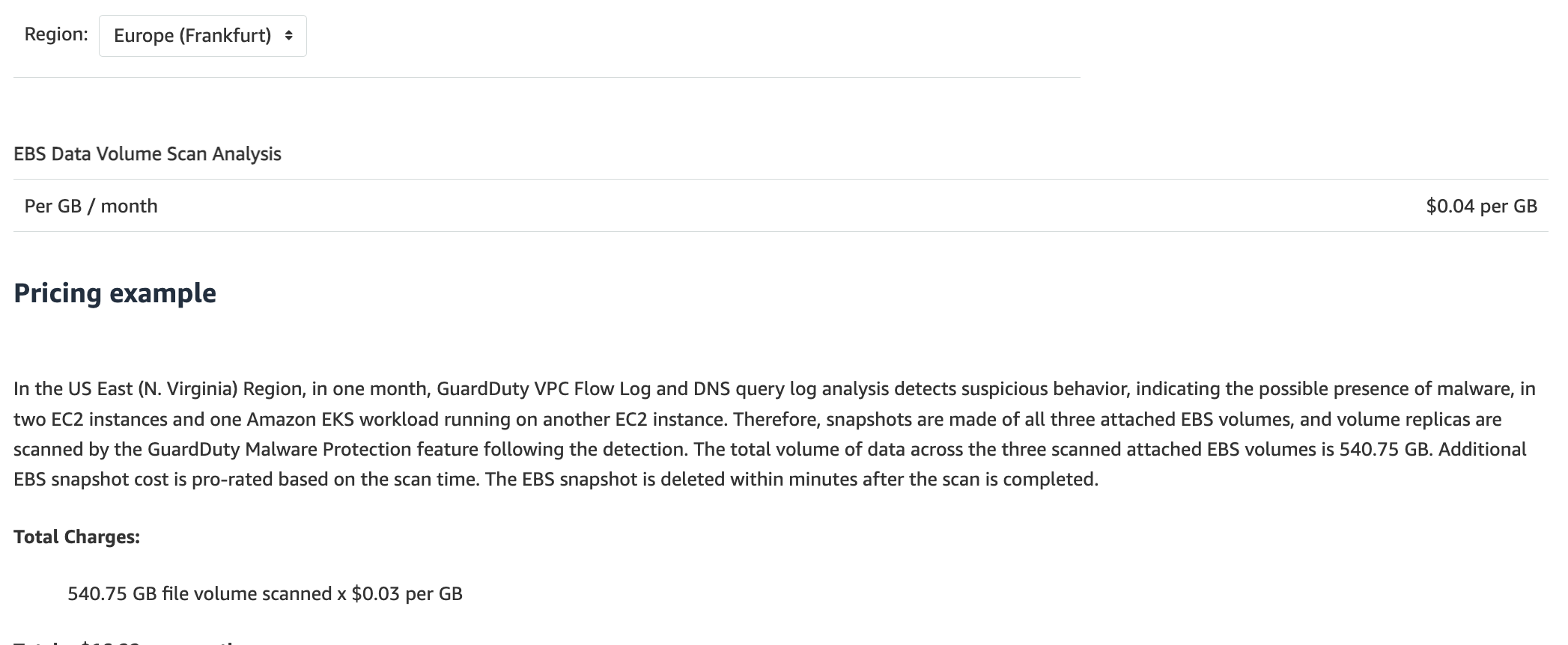
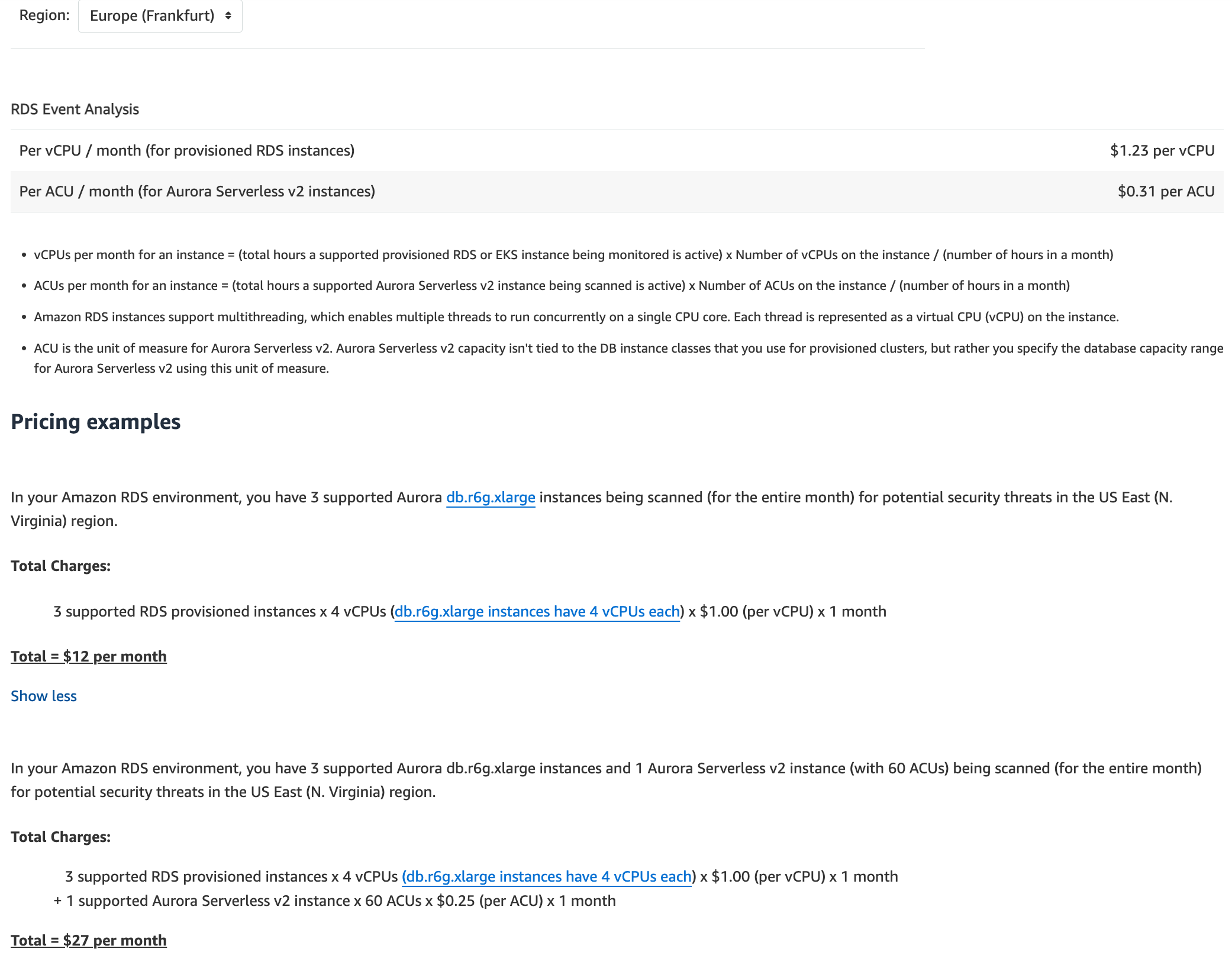
RDS protection - When the GuardDuty RDS Protection feature is turned on, GuardDuty will immediately begin profiling and monitoring login activity to the Aurora databases in your AWS account for potential threats. The charge for GuardDuty RDS Protection is based on the number of protected RDS provisioned instance virtual CPUs (vCPUs) per month. For Aurora Serverless v2 instances, the charge will be based on the number of protected Aurora Serverless v2 instance Aurora capacity units (ACUs) per month
Lambda protection
Expected Outcomes
Implementation of AWS GuardDuty on all Prod and Pre-Prod accounts.