HLD007 - EKS and VPC
Introduction
Purpose
This high-level design document provides an overview of the AWS EKS solution. The primary goal is to ensure that the solution is secure, compliant and following industry best practices.
Changelog
Revision | Date | Description |
|---|---|---|
| 23.07.2024 | Initial document |
Related documents
Background
Amazon Elastic Kubernetes Service (Amazon EKS) is a managed service that you can use to run Kubernetes on AWS without needing to install, operate, and maintain your own Kubernetes control plane or nodes. Kubernetes is an open-source system for automating the deployment, scaling, and management of containerized applications.
High-level architecture
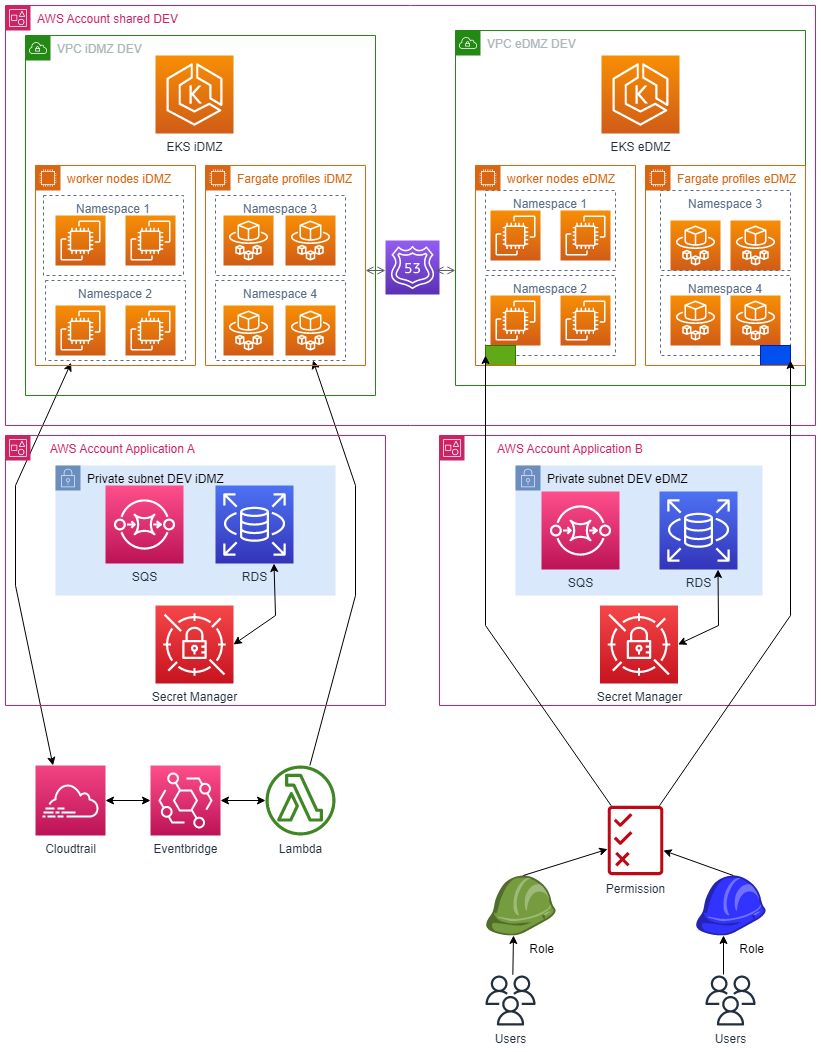
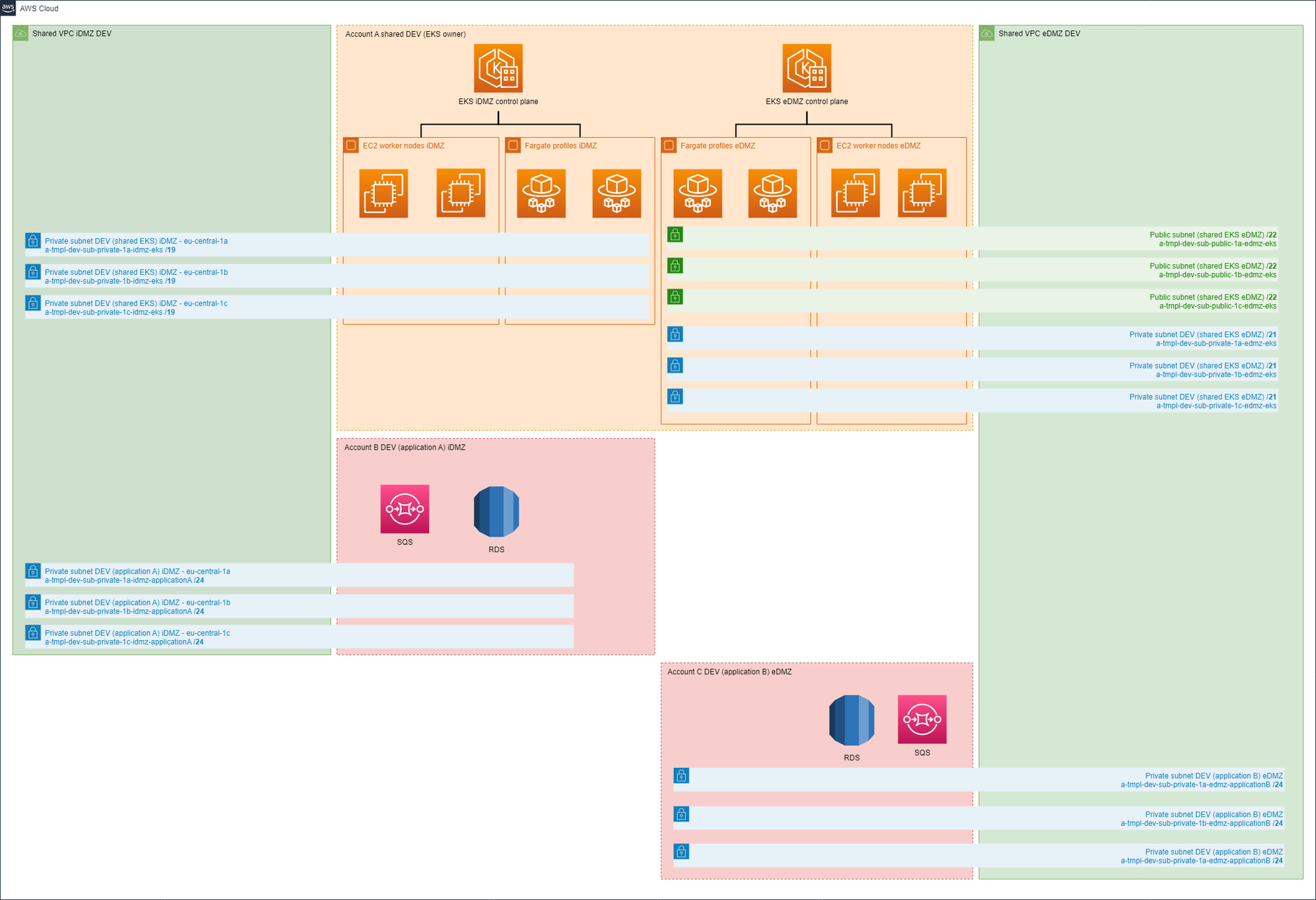
Explanation
The Amazon Elastic Kubernetes Service (EKS) will be established on a main account, serving as the host for the shared Virtual Private Cloud (VPC). This strategic arrangement aims to ensure flawless integration with the Domain Name System (DNS).
In the shared development (DEV) account, key components such as the VPC, EKS Cluster, worker nodes, and Route 53 will be deployed. The worker nodes will be logically grouped within namespaces. This measure is aimed at preventing containers that are not part of the same application from intercommunicating, hence serving as network isolators to a certain degree.
Moreover, we have incorporated distinct permissions for each application. In practical terms, this means that containers within Team A can only be managed by Team A, whereas containers under Team B are solely managed by Team B. This arrangement is demonstrated in the diagram where, for instance, Team Green only has access to pods residing within the green namespace. An identical access arrangement applies to Team Blue.
Furthermore, CloudTrail will be tasked with the important role of collecting administrative logs, enhancing our visibility and control over the system.
In terms of the application layer, it will be deployed to the application account. Specifically, within application account A, we will host services such as Amazon Relational Database Service (RDS), Simple Queue Service (SQS), and the Secrets Manager. The latter will be utilized for storing sensitive credentials required for RDS operations, ensuring a secure and compliant handling of such data.
Expected Outcomes
Implementation of EKS